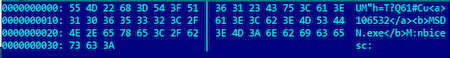Packer: UPX
- SHA1 hash: be4d8344669f73e9620b9060fd87bc519a05617a
Description
A backdoor written in Go and packed via UPX. Investigated backdoor version V2.5.5 z 2021.7.19.
Operating routine
At the beginning of the work, the malicious code checks whether another copy of the backdoor is running. The trojan checks for the [string]c:\windows\inf\mdmslbv.inf[/string] file and, if it exists, starts reading. You can use the following script to decrypt:
import sys
with open(sys.argv[1], 'rb') as f:
d = f.read()
s = bytearray()
for i in range(len(d)):
s.append(d[i])
for i in range(len(s)-2, 0, -1):
s[i] = (((s[i + 1] * s[i + 1]) ^ s[i]) & 0xff)
with open(sys.argv[1] + '.dec', 'wb') as f:
f.write(s)
Encrypted file’s length
The packet’s structure:
- random string from 10 to 19 characters long;
- between the <a>...</a> tags contains the PID of the backdoor process;
- between the <b>...</b> tags is the name of the process;
- random string from 10 to 19 characters long.
The trojan checks for the existence of a process with the specified parameters and, if it finds it, terminates its work.
If a process with the specified parameters or the [string]mdmslbv.inf[/string] file itself was not found, the Trojan generates data as shown above, encrypts and writes to the [string]c:\windows\inf\mdmslbv.inf[/ string].
Communication with the command and control server
The trojan has command and control server: [string] blog[.]globnewsline[.]com [/[/string]]
The trojan sends a GET request to the following URL: [string] hxxps://blog.globnewsline.com:443/db/db.asp [/string] using User-Agent "Mozilla/5.0 (X11; Windows x86_64; rv:70.0) Gecko/20100101 Firefox/70.0". If the server response contains the substring [string] Website under construction [/string], then the trojan considers that the control server is available. If the server is unavailable, the malicious code checks for the presence of a proxy configuration file [string] c:\windows\inf\bksotw.inf [/string] and, if present, reads the parameters written in the file.
The backdoor uses MAC addresses as the network interface bot ID. For heartbeat requests, the following POST requests are used:
https://blog.globnewsline.com:443/db/db.asp?m=w&n=~A<macaddr>.t
where [string] <macaddr> [/string] is the MAC address string, converted to uppercase with colons removed.
Next, a GET request is sent to get a list of commands:
https://blog.globnewsline.com:443/db/A<macaddr>.c
The server response is encrypted in the same way as the file with the PID of the backdoor process.
The following commands can be executed:
- up;
- down;
- bg;
- bgd;
- getinfo.
The result of the command is encrypted in the same way as the command was encrypted, and sent in the body of the POST request to the following URL:
https://blog.globnewsline.com:443/db/A<macaddr>.c