- Packer: absent
- Compilation date:: 16.09.2014 04:15:09
- SHA1 hash: b33e65fd1790260ad47a0dbdad2f12f555a0d6ca
Description
A malicious .DLL library written in C++ and supports the 32- and 64-bit Microsoft Windows operating systems. It is a backdoor that allows attackers to remotely control infected computers via the remote shell―by running cmd.exe and redirecting input-output to their C&C server.
Operating routine
Its original name from the export table is state.dll. It has the Cja and ServiceMain exported functions.
The C&C server address is eye[.]darknightcloud[.]com:443.
This malware is based on the publicly available Gh0st backdoor source code. Compared to the original program, BackDoor.Farfli.130 has noticeably fewer capabilities, but also has several specific features. In this regard, this description will only cover the essential differences from the classic Gh0st RAT.
The C&C server address is encoded with Base64 and encrypted with a simple algorithm:
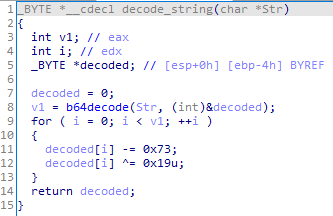
Other encrypted strings are decrypted by subtracting 1 from each byte of the string.
The infected computer ID is stored in the %APPDATA%\wins.tmp file instead of the system registry.
The traffic between the backdoor and C&C server is encrypted using the RC4 algorithm with the following key:
b25lIGluIHRvIE5ldyBZb3JrIHRoYXQgbW9ybmluZyBmb3IgdGhpcyBmZW5jaW5nIG1lZXQgd2l0aCBNY0J1cm5leSBTY2hvb2wuIE9ubHksIHdlIGRpZG4ndCBoYXZlIHRoZSBtZWV0LiBJIGxlZnQgYWxsIHRoZSBmb2lscyBhbmQgZXF1aXBtZW50IGFuZCBzdHVmZiBvbiB0aGUgZ29kZGFtIHN1YndheS4gSXQgd2Fzbid0IGFsbCBteSB
BackDoor.Farfli.130 functionality is limited to the following:
- Obtaining information about storage discs
- Receiving the process list
- Launching the command shell and redirecting input-output to the C&C server
- Shutting down the computer
- Setting the ID of the infected computer.
