Biblioteca de virus
El análisis de tecnologías usadas por los malintencionados nos permite sacar conclusiones sobre los posibles vectores de desarrollo de la industria antivirus y afrontar las futuras amenazas con mayor eficacia. Entérese de cómo funcionan varios programas nocivos en sistemas infectados y cómo afrontarlo.
ePrica in virus library:
| SHA1: | File name | DLL name after decryption | Description |
|---|---|---|---|
| 726613215a29826a33e96486222ec9ff2ad2c077 | setup_4_0_14_6.exe | installer of ePrica 4.0.14.6 | |
| 0bb3f466476e241e5da29fe77775f65bbcb337bc | lx01af01.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 9111571131730e127480036420deef6cd8549638 | lx02af02.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| bff77975cfea2439a46db1c0e09c6d42687ae4b3 | lx03af03.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| f1a7f4144220493576f172ef64ce7f0e4a9f1df9 | lx04af04.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| f104d5e3b2fa88c2fcc81aa88e6f3667d4924277 | lx05af05.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| feef00d7e7903cb3b4548b9e9e02df892797fea3 | lx07af07.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 5f7931c88681c0eb807dbd716601eb2b82978918 | lx10af10.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 634ff6e29558c415849d4d1a1f23d406a41f722e | lx10af20.nlb | installer.dll | BackDoor.Dande.2 with the driver isaPnpPrt |
| 13e3e4f7747476af6016d3a64bbbca74abdb2dbe | lx10af39.nlb | installer.dll | BackDoor.Dande.2 with the driver isaPnpPrt |
| 8120d603bd2019cc36560bb94f76a4c2bbd7160c | lx11af11.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 45ee755c3210e93db8590dd0b1b120164131798c | lx12af12.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 802b5603c7179c27ce1e6d4fdbfbae6db5bc5d93 | lx14af14.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 0b376df2f722f4b15097a4a357dc5afdea628e77 | lx15af15.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| ea89eaacffa8c38ff31e55caaa8463177a249c1f | lx16af16.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| be921123ed231bcc864c92a5a58353974674d1af | lx18af18.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 8a562438d5fdb18482d5a41f2f17b23da9d2ef77 | lx19af19.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| ca67331a469fc1f91fe5ac5dbb045a022c2f46e9 | lx20af20.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 2392507fa6ff223ad125d42a0e1df28a5959a7b6 | lx20af5.nlb | test_pandora.dll | grabber of price lists for SIA International |
| 0d6d3ff8f68351a5bef1d5b827974ae8ab796cb7 | lx22af22.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 34a63864b736f2819a9c02689577de74d53a10ea | lx23af23.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| fceb12b591296fcba0ed5dc682cfa168c935c91b | lx24af24.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 90327f60b94f399a9a1718f94611a97b7f4df46d | lx25af25.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| b5d9306d55d8ccc70a8b88e1c863d4fce0987819 | lx26af26.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 744405c3441a6c37f33ac0b85a994f5ac43cbe82 | lx27af27.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 08a6f14da840bddaac8710da9ef11d8e0d983402 | lx30af30.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 1e7271a192c6336848a48d0c327e8c17731e7c89 | lx31af31.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| f85d9cdd4fd883f9bc840bb2af999d0ec75864fd | lx33af33.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| bbba32c25d9212dfd9eaade8f946d5e8fc6fb6c0 | lx37af37.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| e5e7f98a693f79b630ea78f358c4be0f6f3a2296 | lx39af39.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| abc12800a1260c2d5c10d01a51042429b09642e1 | lx40AA0.nlb | Project2.dll | grabber for AHold32.exe, WinPrice.exe, RSFOrder.exe |
| 784aa1b9f3e450d569f58881df02a6d54fc2b1de | lx40af40.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 503cf82fed9559083ba972e72db6332c2de0488c | lx42af42.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 476900f361a569571d38349c3f4bd32af98d0437 | lx44af44.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 587ed7891b41ae911f80a6c485f0b52bfd504359 | lx50SL1.nlb | rsforder.dll | grabber for AHold32.exe, WinPrice.exe, RSFOrder.exe, tamda.exe |
| c06ad7f64afaff90d4da588b64dbea9f524b842a | lx55Gl92.nlb | Project1.dll | grabber for AHold |
| 4084b8027d876a75cf8fc808ac49ebc60a022424 | lx607cb.nlb | status.dll | collection of information about the system, anti-viruses and check of the installed driver isaPnpPrt.sys of the Dande Trojan |
| 4d1bd71913abe85bc1a86e3abaca1a450cd0ff41 | fe.emd | FE.dll | grabber of price lists |
| a1c9de6599ee6b505de15aba65fc26401dea9a1a | gci.emd | gci.dll | AHold32.exe, Dongos_Client.exe, Alliance Healthcare Russia, WinPrice.exe, FM_Client.exe, RSFOrder.exe, tamda.exe |
| 63a18cf6c11a8b073f9646d73ab8ec3f794380e5 | lx98fc01.emd | fac.dll | grabber of price lists |
| d88e6ffabf52b4c8d27ad8f0da91889309408e76 | lx99ia01.emd | ifc.dll | grabber of price lists |
| 21b0e95f93fdb4c008245417f0897fbcec3acb28 | rwj.emd | rwj.dll | RUSSM |
| 471ca3f6af4bc04d878241aaa1f01a8f494c46e7 | san2.emd | San.dll | grabber szpost.dbf, sztovar.dbf, NSZPOSTID |
| 37eaba2de2b16b23fe99eac4492ea7c86df0e3ef | see.emd | ke.dll | WinPrice.exe |
| 24d51713e45b944ed288f211b102028b0759e0ff | runmod.exe | module of decryption and launch of plug-ins from the memory | |
| 7002f14f42d315f41e4d52d0befbdfd22374cbb5 | emd.kst | private key protected with a password |
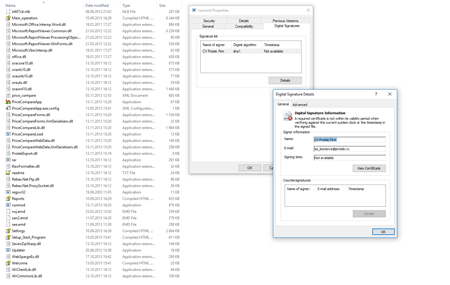
Digital signature of the file runmod.exe:
eZakaz
| SHA1: | File name | DLL name after decryption | Description |
|---|---|---|---|
| 4d4e86391c04029604e90da62f73ed6ab6af3dbd | dkny.emd | dkny.dll | grabber for gaz.exe |
| 4d1bd71913abe85bc1a86e3abaca1a450cd0ff41 | fe.emd | FE.dll | grabber of price lists |
| d0948749bd8164ca9ff11cee0a943b77f5545db5 | gci.emd | gci.dll | AHold32.exe, Dongos_Client.exe, Alliance Healthcare Russia, WinPrice.exe, FM_Client.exe, RSFOrder.exe, tamda.exe |
| ec1ebec5d396a669cac4b54f0c34f95995389d8f | gcif.emd | gcif.dll | grabber of price lists |
| 86af6fcf21a5894f104bc5fc1566b829725e71b9 | gep.emd | ge.dll | grabber of price lists |
| ac479abdfd94aa56d843f96b20f792d85956c4bc | kep.emd | grabber for WinPrice.exe | |
| 145190fe0abaef753c8383e641011b8bc4fd6992 | lx01af01.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| 9a23565402457428973689377b454cb495504aab | lx01rwk.nlb | rwk.dll | grabber RUSSM |
| 400068f63b58f84c5e186aa3bf999d9194c75299 | lx01tu01.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| ea11e708f5a3193173253ecfadfffba31fc4b3f2 | lx05af05.nlb | installer.dll | BackDoor.Dande.2 with the driver RpcSsPrt |
| d77111608915a0e7ba1f6b5549907eab274c68b1 | lx10af1.nlb | starter.dll.dll | Win32.Dande (first version) |
| 2392507fa6ff223ad125d42a0e1df28a5959a7b6 | lx20af5.nlb | test_pandora.dll | grabber of price lists for SIA International |
| 18b61504cd2eb7c53ad5adcedc677cc81fa5bcef | lx20df5.nlb | test_pandora.dll | grabber of price lists for siacli |
| 34b81b0b0bb71114635de01cf62a952bbd6e8a10 | lx40AA0.nlb | Project2.dll | grabber for AHold32.exe, WinPrice.exe, RSFOrder.exe |
| 2c98831cfb73a7ae90420dfb9cfdbfe1f71d5ab2 | lx50SL1.nlb | rsforder.dll | grabber for AHold32.exe, WinPrice.exe, RSFOrder.exe, tamda.exe |
| db28824564fc0a3a47dbfed415b80ed127240d9a | lx55Gl92.nlb | Project1.dll | grabber for AHold |
| 66336f359ed04648a12b8537a9507ac3c15ebdd2 | lx607cb.nlb | status.dll | collection of information about the system and anti-viruses, check of the installed driver isaPnpPrt.sys of the Dande Trojan |
| 31ad2082d21f9cef17de6ab052886406f848fe66 | lx61af01.nlb | pmd.dll | grabber of price lists |
| a1c9fbb3366fec6ad107e0a8daec54fb004c9f18 | lx63zf01.emd | lx63zf01.dll | grabber of price lists for FClient.exe |
| 15f348d73b41933c875374841028403c6c7d7d6c | lx99ia01.emd | ifc.dll | grabber of price lists |
| 8b2f26f2ddd0e0e0ebc1f1490f3152e8c1857264 | rwj.emd | rwj.dll | RUSSM |
| 37eaba2de2b16b23fe99eac4492ea7c86df0e3ef | see.emd | ke.dll | WinPrice.exe |
| 3bc30284dd5285f186dcd29ebf601442f1a4d4bb | zakaz.exe | decrypts plug-ins in the memory and launches them, it is a client part of the program | |
| 7002f14f42d315f41e4d52d0befbdfd22374cbb5 | emd.kst | private key protected with a password | |
| b70ef72af2374fec42fa16ea84620f9503880c61 | DataCollector.dll | oradc32.dll | grabber of price lists from the 1C databases (BackDoor.Dande.62) |
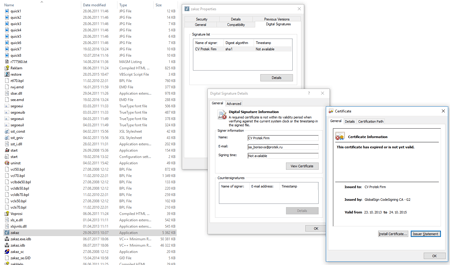
Digital signature of the file zakaz.exe:
Trojan files detected as BackDoor.Dande.63 – BackDoor.Dande.159.
zakaz.exe
Component of the eZakaz application that decrypts its plug-ins using the private key emd.kst and launches them in RAM. It also works with the eZakaz database.
runmod.exe
Component of the ePrica application that decrypts its plug-ins using the private key emd.kst and launches them in RAM. After detection of the key password (“flatron2005”), security researchers were able to decrypt these plug-ins.
oradc32.dll
Plug-in that copies information about medication procurement from the 1C database. To determine the database location, it uses the following thread of the system registry:
[HKEY_CURRENT_USER\Software\1C\1Cv7\7.7\Titles]
Scans directories and searches them for databases with the following names: 1Cv7.MD and 1Cv7.DD. If they are detected, it searches them for the TaskItem key and checks the availability of the word “pharma”. The plug-in saves information on the path to the found databases.
It also tries to find databases called RA844.DBF and RA1227.DBF. If they are detected, it performs their syntactic analysis (parsing).
It saves a report to the file oradc32.st that is compressed by the zlib library.
After removal of ePrica, the Trojan modules remain on the infected computer and continue their operation.
Vulnerabilidades para Android
Según las estadísticas, cada quinto programa para el SO Android tiene vulnerabilidades, lo cual les permite a los malintencionados implementar los troyanos móviles en el dispositivo y realizar las acciones necesarias.
Auditor de seguridad en Dr.Web para Android diagnosticará y analizará la seguridad de un dispositivo móvil, ofrecerá soluciones para resolver los problemas y las vulnerabilidades encontrados.