Biblioteca de virus
El análisis de tecnologías usadas por los malintencionados nos permite sacar conclusiones sobre los posibles vectores de desarrollo de la industria antivirus y afrontar las futuras amenazas con mayor eficacia. Entérese de cómo funcionan varios programas nocivos en sistemas infectados y cómo afrontarlo.
Program.Algo360 in virus library:
Program.Algo360 is a special SDK designed to create users’ credit score based on their personal data. This software module is popular among Indian financial organizations which integrate it into their apps.
Depending on it’s version, module collects various information. Collected data is accumulated in JSON files, packed into ZIP archive and then uploaded onto developer’s server.
Among all known modifications of this SDK, the largest amount of data is collected by the module built into the Eduvanz application. Further example below will be based on this particular app.
- SHA1: bc05ccaee5298f4e46fdccf73c1f1903fcb05432
- Package name: com.eduvanzapplication
- Version: 5.1.5
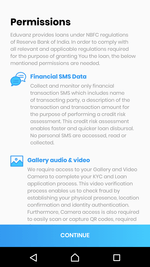
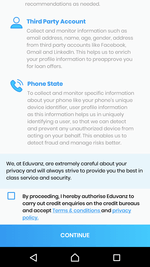
Upon first launch the app notifies user about collecting data and asks to agree with terms and conditions:
Program.Algo360 module built into it collects the information as follows:
- SMS, if one of the following conditions is met:
- mobile phone number is based on 10 or less digits;
- mobile phone number does not have +91 sequence in it. As a result, module will collect information about SMS received from any mobile numbers but the Indian mobile numbers;
- names and types of all user accounts stored on the device;
- the list of installed applications and Internet usage statistics for each of them;
- the information about the device: device model name, manufacturer, IMEI, mobile operator name;
- battery status: current time, charge level, whenever the USB cable is plugged in;
- web browser bookmarks: title, url, creation date;
- user calendar entries: events participants (their email, names, status), header, time, organizer, ID;
- calls log: phone number, calling date, the lengh and the type of the call, entry ID in the calls log;
- contacts from the phone book: name, phone number;
- device geolocation information, and
- SIM card data: slot which is currently in use, IMSI, IMEI, mobile operator name, mobile phone number, current time.
Vulnerabilidades para Android
Según las estadísticas, cada quinto programa para el SO Android tiene vulnerabilidades, lo cual les permite a los malintencionados implementar los troyanos móviles en el dispositivo y realizar las acciones necesarias.
Auditor de seguridad en Dr.Web para Android diagnosticará y analizará la seguridad de un dispositivo móvil, ofrecerá soluciones para resolver los problemas y las vulnerabilidades encontrados.